Introduction:
In today's interconnected world, security is paramount, especially when it comes to authenticating and authorizing users in web applications. JSON Web Tokens (JWT) have emerged as a popular method for securely transmitting information between parties in a compact and self-contained manner. In this blog post, we'll delve into the intricacies of JWT, exploring what they are, how they work, and why they're essential in modern web development.
What is a JSON Web Token (JWT)? JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. JWTs are commonly used for authentication and information exchange in web applications.
Components of a JWT: A JWT typically consists of three parts separated by dots (.), which are:
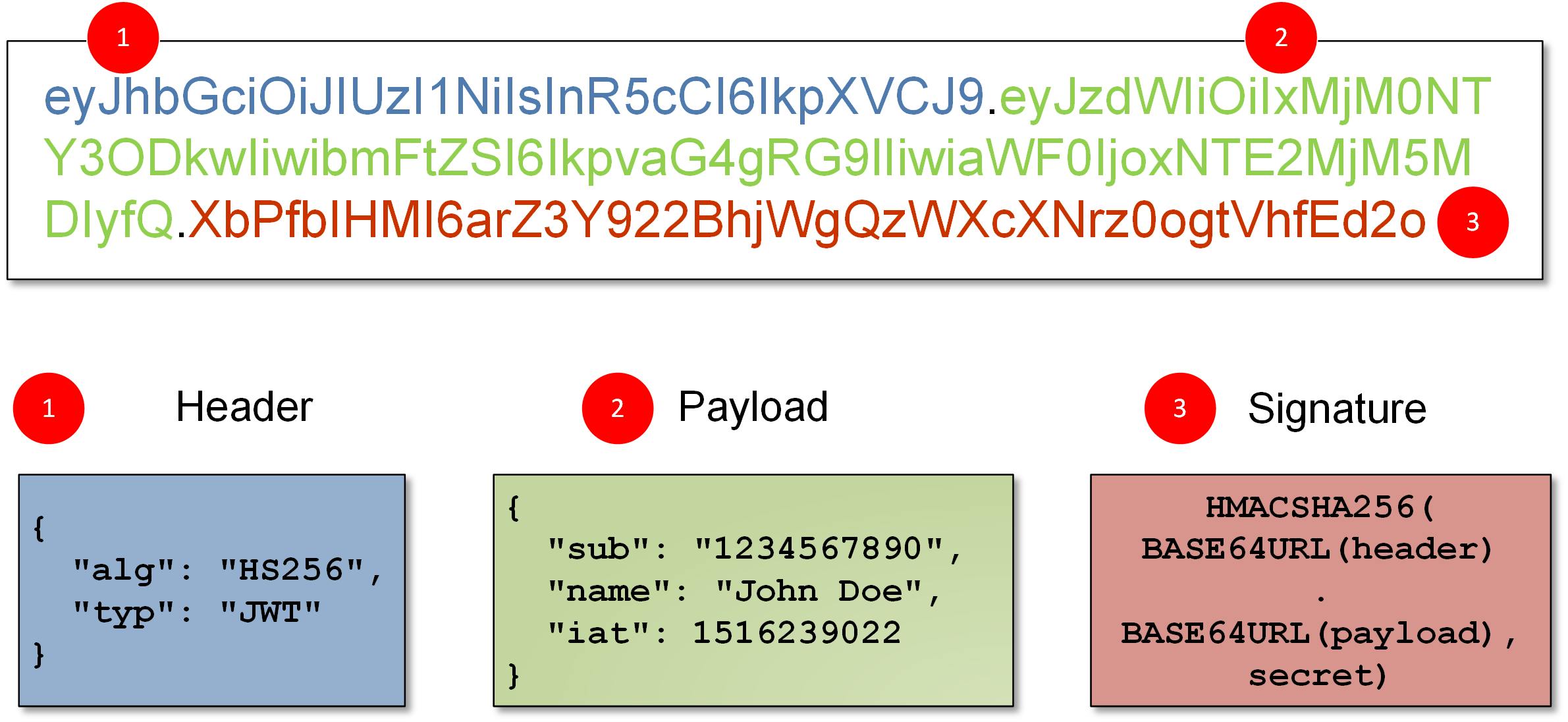
Header: Contains metadata about the token, such as the type of token (JWT) and the signing algorithm used.
Payload: Contains the claims, which are statements about an entity (e.g., user) and additional data. Claims can be categorized as reserved, public, and private claims.
Signature: Used to verify that the sender of the JWT is who it claims to be and to ensure that the message wasn't tampered with during transmission.
How JWT Works:
Authentication: When a user logs in to a web application, the server generates a JWT containing the user's identity (claims) and signs it with a secret key.
Authorization: The client receives the JWT and includes it in subsequent requests to the server, typically in the Authorization header as a Bearer token.
Verification: Upon receiving a JWT from the client, the server validates the token's signature to ensure its authenticity and integrity. If the signature is valid, the server extracts the claims and performs authorization checks based on the user's permissions.
Benefits of Using JWT:
Statelessness: JWTs are self-contained, meaning they contain all the necessary information within the token itself. This eliminates the need to store session state on the server, resulting in scalable and stateless architecture.
Cross-domain Usage: JWTs can be securely transmitted across different domains and platforms, making them ideal for building distributed systems and microservices architectures.
Security: JWTs use digital signatures to ensure data integrity and prevent tampering. Additionally, JWTs can be encrypted to protect sensitive information within the token.
Best Practices for Using JWT:
Use HTTPS: Always transmit JWTs over HTTPS to encrypt the data in transit and prevent eavesdropping.
Keep Tokens Short-Lived: Set expiration (exp) claims in JWTs to limit their validity period and mitigate the risk of token misuse.
Use Secure Signing Algorithms: Choose strong cryptographic algorithms (e.g., HMAC, RSA) and secure key management practices to protect JWT signatures from attacks.
Conclusion: JSON Web Tokens (JWT) have become a popular choice for implementing authentication and authorization mechanisms in modern web applications. By understanding the structure, working principles, and best practices associated with JWT, developers can build secure, scalable, and interoperable systems that meet the demands of today's digital landscape. Whether you're building a single-page application, a RESTful API, or a microservices architecture, JWTs provide a versatile and effective solution for securely transmitting information between parties.
